Our Blog - page 26
Pay or Die: New Ransomware Comes to Hit Your Computers. Are You Ready to Fight Back?
Ransomware, a kind of malware that has become a real curse for the companies and organizations around the world, comes in a new, much sneakier and more dangerous disguise. New malware is called Fonix and it’s able to turn your endpoints into the useless bricks ruthlessly depriving you of access to all your data. It…
Read MoreQ3 Cyberattacks and Trends: Social Engineering Takes the Upper Hand
COVID-19 strikes almost everything in the world, and the cybersecurity field is not an exclusion. Observing the Q3 events and incidents makes obvious the fact that Coronavirus has cardinally changed the world’s cybersecurity landscape and these changes look irreversible for the nearest future. More of that, these new trends seem to be able to distinguish…
Read MoreTOR Network Under Sophisticated Attack: Perpetrators Covertly Steal Users’ Bitcoins
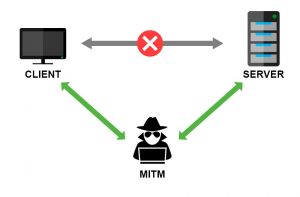
Many people around the world deeply believe that using the Tor browser brings them unbeatable security and total anonymity. In reality, this belief puts you in danger. And a recent cunning attack on Tor users sharply demonstrates this fact. Many users who employed Tor to manage their cryptocurrency accounts fell prey to this attack. And…
Read MoreHow to Avoid Being Hacked Like Twitter: Fatal Mistakes You Should Correct Immediately
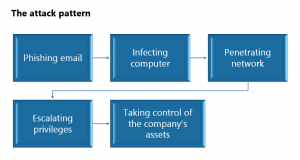
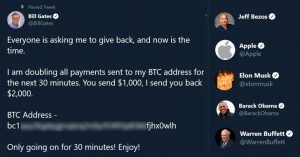
The recent Twitter hack quickly became one of the top news in the world. And there are at least two solid reasons for this. Firstly, the security system of such a powerful company as Twitter occurred to be flawed. Secondly, the attackers were able to break into accounts of the most powerful people of the…
Read MoreUpdated and more dangerous: FakeSpy comes back to steal money from Android devices
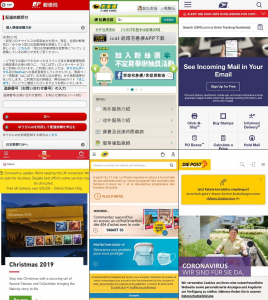
Have you received an SMS from your postal service that says you’ve got a package and should click on the included link for more information? Don’t do that! Otherwise, your smartphone will be brought under the total control of cybercriminals. They try to infect your device with a cunning malware named FakeSpy. Earlier such attacks…
Read More