How to Avoid Being Hacked Like Twitter: Fatal Mistakes You Should Correct Immediately
The recent Twitter hack quickly became one of the top news in the world. And there are at least two solid reasons for this. Firstly, the security system of such a powerful company as Twitter occurred to be flawed. Secondly, the attackers were able to break into accounts of the most powerful people of the world with frightening ease. Inevitably, the question arises: if such a powerful entity can be hacked with such ease, might we believe that average companies and people are really secure today?
That’s why it’s especially important for the cybersecurity community to deeply elaborate on this attack and learn lessons for the future to prevent assaults of this kind. Here is the DIESEC analysis of the situation and our recommendations on your protection.
The attack: Would you like to double your money?
On a one splendid July day, followers of Bill Gates discovered an unusual tweet, promising them to double any sum sent to the given bitcoin address. They were not alone. The same text appeared in the accounts of many celebrities, top businessmen, blue-chip companies and politicians, including Elon Musk, Barack Obama, Jeff Bezos, Mike Bloomberg, Joe Biden, Apple, Warren Buffet, etc.
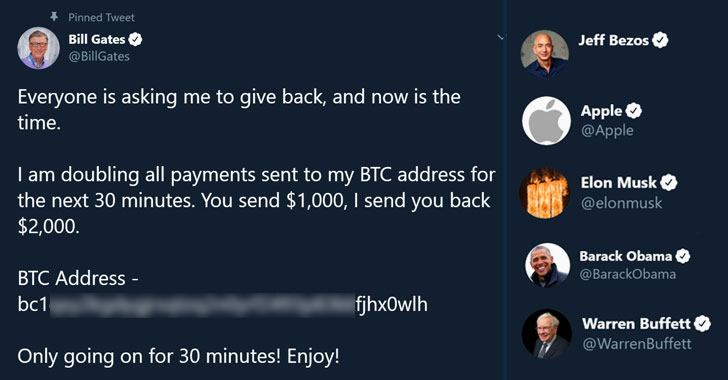
Of course, the owners of those accounts did not write those tweets. The accounts were hacked. And it is, probably, the most stunning and massive attack on powers-that-be and celebrities for the moment. “We’re embarrassed, we’re disappointed, and more than anything, we’re sorry. We know that we must work to regain your trust, and we will support all efforts to bring the perpetrators to justice,” Twitter wrote in their blog.
And they really have solid reasons for “disappointment”. Many observers are wondering: What the consequences would be if the attackers were not just scammers looking for some cash but terrorists or psychopaths wanting to wreak havoc and panic?
The attackers: Exploiting human vulnerabilities
Soon FBI busted the supposed attackers. The feds have accused three young men: 17-year-old Graham Clark, 19-year-old Mason Sheppard, and 22-year-old Nima Fazeli. And here is the spot where interesting nuances appear.
According to the FBI, some of the detained were accused of fraudulent actions before. But they don’t look like technically advanced super-hackers. And it’s a very important point to take into consideration. This staggering attack was not based on sophisticated techniques of computer hacking but social engineering tricks. In other words, it was not hacking computers — it was hacking of human minds.
Why do we want to stress this point? Because it clearly reflects the current situation in the cybersecurity field: Most attacks are targeted at humans, and today there are not enough tools to protect from attacks of such kind. At least, much less than from tech-based assaults.
We suppose the Twitter network environment and web-applications have the best defensive equipment possible. But as you can see, it goes useless when it comes to human vulnerabilities.
The most impressive thing about this attack is that some people with fraudster skills could easily break into one of the most powerful tech companies in the world. And what is more impressive, their tricks were not so sophisticated. They broke into Twitter in just two steps.
Let’s look at them closely.
The method: from Slack to spear-phishing
As Twitter discloses the attack details rather reluctantly and sparingly, we’ve based our research on the most influent media reports.
As NYT reported, one of the attackers “… got access to the Twitter credentials when he found a way into Twitter’s internal Slack messaging channel and saw them posted there, along with a service that gave him access to the company’s servers”.
That is an epic fail number one. If you save credentials in this way, being hacked is just a matter of time.
But wait… just credentials must not be enough to enter the Twitter internal network. It must have a two-factor (2FA) authentication, right?
Right. And that’s why the perpetrators made use of social engineering. They conducted a spear phishing phone attack to get the information from Twitter’s employees. What is especially interesting, they used the as-old-as-time trick: as Reuter reported, the caller pretended to be a co-worker from the IT department and convinced the employee to share credentials.
Can we call it a refined and sophisticated attack? Unlikely. In fact, “easy-peasy” sounds much more applicable.
Let’s sum up now. Three young men, one of which underage, without applying deep technical knowledge, hacked one of the most powerful tech companies and took control over accounts of the most powerful people on the Earth.
Don’t you think there is something wrong with the approach to cybersecurity, do you?
Lessons to learn: Strengthen the human factor
A few obvious questions inevitably arise here. What mistakes and flaws in Twitter’s defense line made the attack successful? How can they be corrected in the future? Was it possible to prevent the attack?
Based on the information above, we can make a clear conclusion: the attackers succeeded because Twitter’s security approach and implementation were not corresponding to top-security standards. Here is why.
Firstly, it’s obvious that their security policies and procedures were not implemented or at least followed correctly. Storing credentials into a Slack account is a definitely rude violation of general security rules.
The other security drawback is giving access to a wide range of people. As Reuter reported, “More than a thousand of Twitter employees and contractors as of earlier this year had access to internal tools that could change user account settings and hand control to others, two former employees said”. Here we can see the rude violation of Access Control rules. The correct approach supposes limiting access to only the necessary number of employees.
And the icing on the cake. The social engineering trick with “a colleague from IT-department” is so old and trivial that is considered a classic example of SE and explained on any decent security training. Frankly, it looks rather strange for employees of such a solid company to buy into that.
As we can see here, the attackers succeed not because of their refined sophisticated hacking skills but because the company neglected some important security rules. What is important to notice, those rules don’t relate to networks and web-applications but a human factor.
How you can avoid falling prey like Twitter
Firstly, you should elaborate and implement strict policies and procedures about passwords, including its storing and secure handling.
Secondly, you need to apply strict Access Control rules, particularly the principle of least privilege that allows a user to work only with functions necessary for his/her duties.
Thirdly, conduct a decent training of employees on counter social engineering skills. As a result, your employees must be able to spot most kinds of social engineering attacks and take correct action to stop or mitigate the attack immediately. That is how we in the DIESEC train staff of our clients.
Yes, just these three simple steps taken promptly could save Twitter from the shame and troubles they have today.
And now… is not it a good time to ask yourself the crucial questions: Are my business facilities protected good enough? Cannot the sad Twitter story repeat in my company environment?
Live informed and secure with DIESEC!
