Pay or Die: New Ransomware Comes to Hit Your Computers. Are You Ready to Fight Back?
Ransomware, a kind of malware that has become a real curse for the companies and organizations around the world, comes in a new, much sneakier and more dangerous disguise. New malware is called Fonix and it’s able to turn your endpoints into the useless bricks ruthlessly depriving you of access to all your data. It can paralyze all working processes of your company and plummet your business. Here is how.
Ransomware is a well-known top-dangerous enemy. There is a diversity of ransomware types but all of them do the same kind of harm: Encrypt files on victims’ computers and extorts a ransom to decrypt it. For the last years, many companies and state organizations fell prey to ransomware attacks and experienced that extremely obnoxious feeling of total helplessness in the face of perpetrators. Because for many companies who did not care about having backups this attack leaves a narrow choice: pay or die.
Aimed at the same purpose, Fonix is quite different from its predecessors by many traits. Firstly, it does not spread in a habitual way. It’s RaaS or Ransomware-as-a-Service.
What does it mean?
Like a legal SaaS (Software-as-a-Service) model, RaaS spreads via subscription. A criminal-to-be buys access to a ransomware framework and manages it from there to conduct attacks. Strange, but Fonix model does not work this way. All communication with its authors is conducted via email. Here is how exactly.
A criminal-to-be sends an email to the address pointed in a Fonix advertisement. His message includes the email he wants to use in Fonix attacks. The malware author sends him Fonix payload connected with the buyers’ email address for victims to get in touch. If the attack is successful and the victim is ready to pay, she contacts the buyer of Fonix. The buyer, in his turn, contacts with the author again, now to decrypt the files.
But how exactly it attacks?
How Fonix can hit your assets
Fonix is advertised at many cybercriminal forums, including the dark web. After getting the payload from the authors, an attacker can spread it via various internet-resources and methods to deliver it to victims. It may include phishing emails, torrent trackers, pirated software, faked legal software files, – actually, anything that makes a user download and run the malicious file. As with other ransomware, the main purpose is to make a victim click on the malicious file – and the job is done.
What harm Fonix does
Being ransomware, Fonix does the same thing as its brothers-in-crime do: Encrypts files on your computers and extort paying a ransom to decrypt them. But unlike most of its brothers-in-crime, it encrypts all files on the attacked system except critical Windows system files. More of that, according to the SentinelLab analysis, this cunning malware uses four different types of encryption: AES, Chacha, RSA, and Salsa20 simultaneously. This combination of reliable encrypting algorithms turns any effort to decrypt the files into a dead case. As an icing on the top, it changes extensions of the encrypted files and hard drives names into.XINOF ( FONIX backward) as a tool to stress that the computer is at the mercy of the attacker.
But this is only the start of the sneaky criminal game. After the victims’ files are pawned, she gets a ransom note. And here the most interesting things happen.
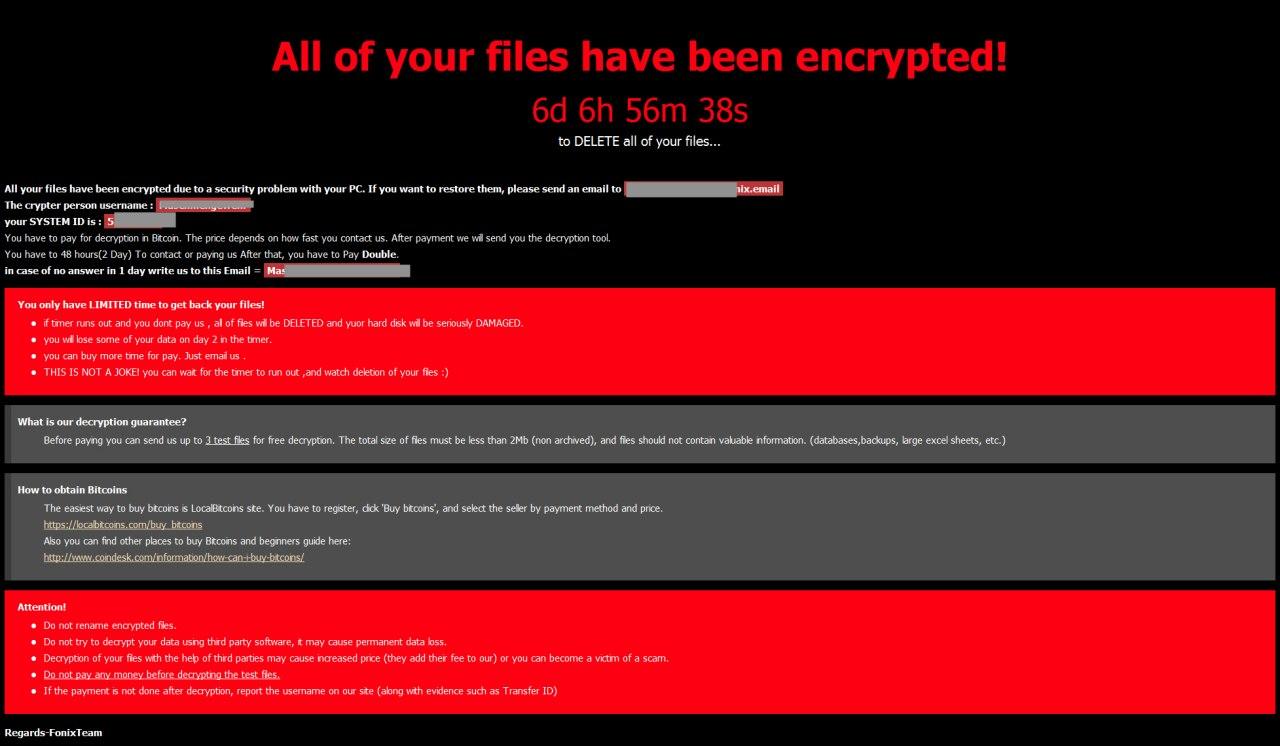
Source: labs.sentinelone.com
How Fonix works
After a victim clicks the infected file, it starts running its malicious mission. Besides encrypting the victims’ files, Fonix sneaks into the Startup folder and registry and create a hidden service to make its presence persistent on the infected machine. It deletes Volume Shadow Copies to prevent the files recovery. It impacts system recovery and safe boot processes. All of this is aimed to deprive victims of any possibility to regain their access to the encrypted files without the participation of the attackers.
After the dark job is done, the computer of a victim is blocked, and a ransom banner appears. To have the files decrypted, a victim should contact the attacker via email and send him “up to 3 files” to get assured that decryption is possible if he will pay the ransom.
But, unlike other ransomware cases, the attacker can’t decrypt the files himself. Nor he exactly knows how to do it, neither has a proper tool for it. Actually, he acts as an intermediary: He sends the files to the authors of the Fonix, who decrypts the victim’s file and sends it back to the attacker. Then the attacker sends the decrypted file to the victim. Thus, the victim gets proof that recovering his files is possible and pays the ransom to the attacker. Then the attacker transfers 25% of the ransom to the authors’ bitcoin wallet. In reply, the author provides the attackers with a decryption key and software. Finally, the attacker sends it to the victim.
At first glance, this long chain looks rather weird and no doubt is much slower than regular Ransomware-as-a-Service instances. For what reasons do the perpetrators use such a strange approach?
The most obvious reason here can be the authors’ desire to secure themselves from a law enforcement investigation: It’s much harder to find and bust them because every attacker acts as a proxy between the author and a victim.
But that’s not all.
In fact, all of this reminds a passive income business-scheme. The Fonix creators are not involved in the attacks directly but got a solid sum from every attack, which let them a possibility to multiply their criminal profit almost without efforts. To sum up, the Fonix creators make others pull chestnuts out of the fire for them.
Unfortunately, this scheme can attract many criminals, especially those who don’t have technical skills but look forward to committing a cybercrime. And it’s a very dangerous trend. If this model becomes popular, the cybercrime around the world will grow exponentially. Why? Because even criminals with minimum computer knowledge can participate in malicious campaigns like that one.
How to protect from Fonix
First of all, we should mention that for the moment Fonix attacks only Windows-based computers. Cybercriminals may use many variants of its dissemination, including social engineering tricks, so it can be caught in a variety of ways throughout the Internet.
However, basic cybersecurity hygiene rules decrease meaningfully chances to be infected. The rules include avoiding pirate software and downloading files from unsolicited resources as well as having antivirus and all software on your machine updated. Certainly, the most dangerous vector of the Fonix attack is social engineering, because even a security-awareness person can be tricked into running a malicious file. Correspondently, a proper Anti-Social Engineering training of your employees will cut the chances of the perpetrators down and significantly raise your chances to stay safe.
And of course, as in any case dealing with ransomware, properly stored backups are the best and the most reliable way to keep your data unharmed and available.
Live informed and secure with DIESEC!
