TOR Network Under Sophisticated Attack: Perpetrators Covertly Steal Users’ Bitcoins
Many people around the world deeply believe that using the Tor browser brings them unbeatable security and total anonymity. In reality, this belief puts you in danger. And a recent cunning attack on Tor users sharply demonstrates this fact.
Many users who employed Tor to manage their cryptocurrency accounts fell prey to this attack. And the most shocking thing is that this sophisticated multilevel assault can’t be totally stopped even now, when cybersecurity specialists are aware of it.
The attack: Three levels of Danger
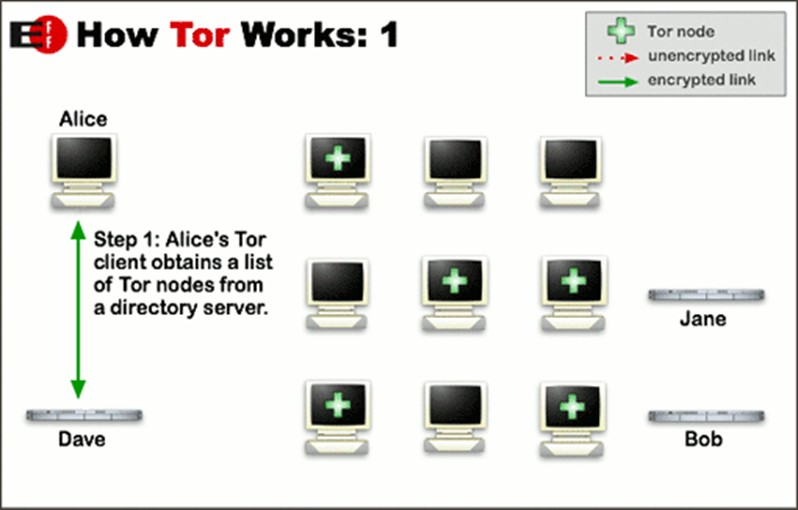
To dissect this sneaky attack, let’s remind how the TOR network works to provide privacy and anonymity for its users.
Unlike regular browsers, Tor uses its network with .onion extension at the end of the address. And, unlike regular browsers, it chooses not the shortest but a complicated and tricky way from a client to a server. The traffic in the Tor network wanders between relays or so-called nodes. Every node knows only the address of the previous node and the address of the next node, so any node does not know the whole pathway of the traffic. To make it more secure, the nodes for a route are chosen randomly.
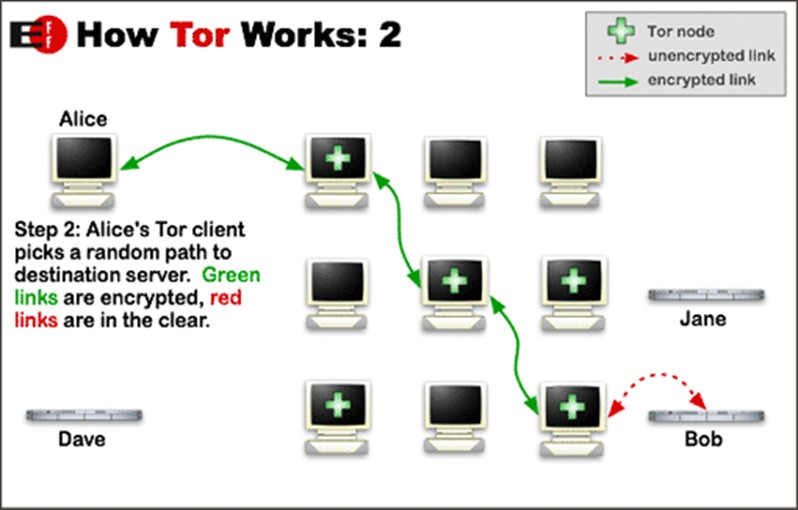
More of that, all traffic is encrypted with separate keys for every hop between nodes.
The result is obvious: No one can trace you or intercept your data with such sophisticated privacy protection, right? But… in reality, everything has its weak points and there is always someone able to detect these points.
In this case, the weak point occurred to be exit nodes –the last nodes a client passes through before connecting to the requested server.
It’s worth mentioning that everyone can contribute to the Tor network development by voluntarily adding their computers as nodes. It sounds good – and partially it is, because the more nodes the network has the better it functions. But the perpetrators used this specificity as a vulnerability and exploited it.
They added quite a few — actually, as much as 23,9% of the entire network on its peak — their nodes to the Tor network. Then, as they had total control over those nodes, it was easy to deploy software for conducting a Man-in-the-Middle attack on the traffic passing via those nodes.
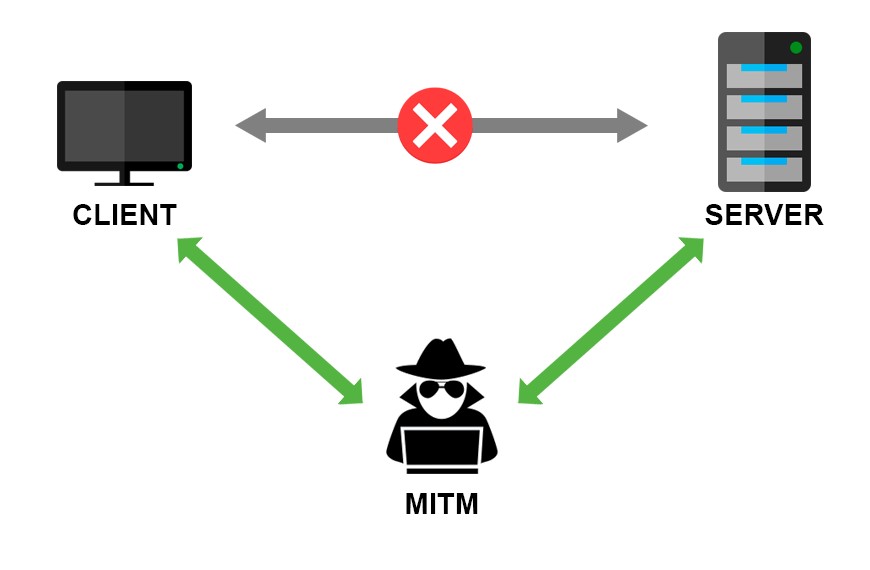
Man-in-the Middle is an attack where the attacker secretly intercepts (and possibly alters) communications between two parties who believe that they are directly communicating with each other.
But you can say that intercepting traffic is useless if it’s encrypted. And nowadays most websites use SSL-encrypted connection. So even with the controlled nodes the attackers must be left in the dust, right? Yes, they definitely would have, if they had not utilized one more kind of attack called SSL strip.
What does the SSL strip attack do? Exactly what it sounds: It strips the SSL protection, or, in other words, downgrades the secure HTTPS connection to insecure HTTP connection, so the interceptor can read all victims’ traffic, including credentials and other secret information.
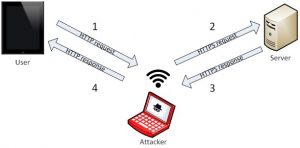
And don’t forget that the cybercriminals are able not only to see but change this traffic also. So, the last point the attackers need to do is detect a bitcoin wallet address in the traffic and change it for their own. Thus, all bitcoins go to their account – and the victims are not even aware of it.
How to prevent this attack: Clients are helpless
The attack is tricky to prevent from many points of view. Firstly, a victim usually has no clue that something wrong has happened. He runs Tor, connects to the website, makes a transaction – and bitcoin are gone forever. What is even worse, a user can’t do anything to prevent such situation because it’s just impossible from the client side. Meantime, the Tor team also cannot help much. As they frankly say, “throughout we kick out malicious relays as soon as we discover them, we are still under capacity to be able to monitor the network and to identify malicious relays”.
The only ones able to prevent SSL-strip attacks are website owners. They should implement HSTS (HTTP Strict Transport Security) policy that forbids opening pages with an HTTP connection. In other words, the server will drop any connection that does not use the secure HTTPS protocol. The most advanced web-resources already use this approach (for example, you can’t conduct an SSL-strip attack against Facebook), and we highly recommend using it in any case dealing with transferring secret information like credentials.
And of course, for a financial institution this approach is a must.
Live informed and secure with DIESEC!
