Updated and more dangerous: FakeSpy comes back to steal money from Android devices
Have you received an SMS from your postal service that says you’ve got a package and should click on the included link for more information? Don’t do that! Otherwise, your smartphone will be brought under the total control of cybercriminals. They try to infect your device with a cunning malware named FakeSpy. Earlier such attacks spikes happened in 2017 and 2018. Those times they were aimed only at Asia countries. But in July 2020 FakeSpy comes back in a new disguise with updated malicious abilities. And the scope of its targets is much wider now. Current FakeSpy attacks are being noticed in France, Switzerland, Germany, United Kingdom, United States, China and Taiwan.
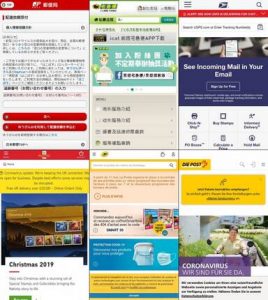
Source: Cybereason
How it harms
After installing on a victim’s device, FakeSpy starts its malicious activity from gathering private information including the contact list, phone number, device’s IMEI, mobile network provider, registered accounts, etc. Then it sends this data to the attackers’ Command&Control server. It takes SMS on the infected device under total control (reading, receiving and sending) and gets access to the information on the external storage. To top it off, it intercepts every incoming SMS and sends it to the attackers’ servers, including the message body, phone of the sender and time of receiving it. It also checks the infected device for the presence of banking and cryptocurrency applications and looks into the NPKI (National Public Key Infrastructure) folder to extract certificates related to financial transactions.
All of the above gives us a solid reason to conclude that the main purpose of this malware is stealing financial information from victims’ accounts. But what makes this malware especially dangerous is the cunning way of its dissemination.
How it spreads
FakeSpy is dissiminated via the SMS phishing (smishing) attacks. A victim receives an SMS that informs her that the local postal service tried to deliver a package but did not catch her at home, and she will find the details by the added link. Hooked up with curiosity, the victim clicks the link and gets to the postal service website with a prompt to install the postal service application. As you probably guess, the website is phishing and the application, in reality, is a FakeSpy malware.
But what is really impressive here is the scale and scope of the attack. The malware has a wide range of different guises to imitate postal services according to the country where the victim lives. There are versions camouflaged as United States Postal Service, Royal Mail, Deutsche Post, La Poste, Japan Post, Yamato Transport, Chunghwa Post, Swiss Post…
These postal companies are well-known and widely used by clients, so there is no doubt that many people around the world will fall prey to this scam. They will find the SMS plausible and decide to install the “postal” application, with all sad consequences.
After installing, the malicious app requires a wide range of permissions that allow it to get plenty of private information and manage the device. If the permissions are given, FakeSpy starts its malicious job.
But that’s not all. Even after taking total control over the infected device, FakeSpy does not stop. It continues propagating itself by automatically sending the malicious SMS to all contacts of the victim, thus turning the infection process into a never-ending story.
One more interesting nuance is that the malware has an embedded protection from security analysis and dissection. After running, it checks the environment. And if it discovers that the environment is not a real Android device but just an emulator (that is often used by security specialists to analyze suspected files), it stops the installation and deletes itself.
To sum up the above information, we come to the conclusion that FakeSpy is carefully made information stealer with a pack of additional spyware functions. Taking into consideration that the creation of such malware costs a pretty penny, we should expect its development will be continued and new spikes of the attack will happen in the nearest future. And they will embrace much more countries and regions.
How to protect from FakeSpy
The weak spot of this malware is that it totally depends on the human factor and social engineering. If you don’t buy into the scam with the installation of “postal application”, the SMS won’t harm you. More of that, if you follow basic general security rules like “Never install an application from any source except Google Play” and “Don’t give an app more permissions that it needs to perform its tasks”, you also won’t fall prey of this attack. The problem here is that many people are not aware of these basic rules or can forget about them when the malicious SMS drops on their devices.
But you, after reading this article, are not one of them. Now you know how to stop a FakeSpy attack and protect yourself.
Live informed and secure with DIESEC!
