OWASP Top 10 2021: Control Access, Encrypt Everything and Be Afraid of Design Flaws
OWASP released a new top 10. What does it mean for your application security?
owasp.org
OWASP Foundation, the most authoritative organization in web-application security, released a new Top 10 of the current threats. The changes are significant and really impressive, sharply illustrating that since the COVID-19 outbreak the cyberspace has become an even more dangerous place, with more sophisticated and hard-to-prevent attacks.
How to protect your web applications in the changed cyberspace by the new standards? Read the following analysis of OWASP novelties from the DIESEC’s experts.
A01:2021-Broken Access Control
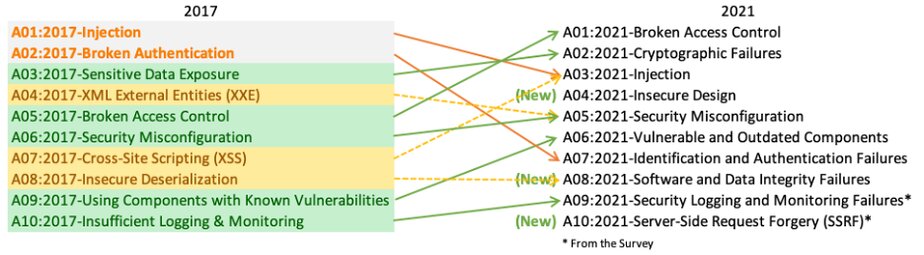
The impressive changes start from the first lines of the new list. The first two positions that had stayed the same since OWASP top 10 2010, Injection and Broken Authentication, gave way to Broken Access control and Cryptographic Failures.
What does it mean. For many years, injections have been the number 1 threat to web applications, and for a solid reason: there is plenty of insecure code relating to users’ input in web applications around cyberspace. But, despite the extreme danger and devastation made by such attacks, it is rather easy to prevent most of them just by providing a proper input validation. Make your code secure – and voila: you are protected from the injection attacks, except extremely sophisticated and cunning ones.
But with Broken Access Control that took the fifth position in the top 10 2017 things become much more complicated. BAC makes the cost clear to unauthorized information disclosure, modification, destruction of data, exploiting business functions of an application in a malicious way. And there is no one common reason for this kind of threat. It can be found in different parts of a web application and as a result, requires more effort to prevent. And it gives cybercriminals a much wider attack surface.
A02:2021-Cryptographic Failures
The next point, Encrypting Failure, is actually renamed number 3 “Sensitive Data Exposure” from the top 10 2017 list. As OWASP itself explains it, this renaming better describes the root cause of this kind of vulnerability and makes the audience concentrate on cryptography as the main means to prevent threats of this type.
What does it mean. Actually, there is not too much to add here. Just that the good old rule of top cybersecurity experts “Encrypt everything you can encrypt” has become even more imperative.
A03:2021-Injection
Point 3 in the top 2021 list is occupied by Injection that descended from first place in top 2017. But it’s not the same as the previous one. Now it includes Cross-Site Scripting (XSS) vulnerability, which always was a separate point in the previous OWASP lists and took the 7th point in top 10 2017.
What does it mean. Adding XSS to Injections collection looks like a totally logical step, because, actually, XSS is (and has always been) a kind of injection, so allocating it in a separate point looked a bit weird. Now the order of how things work is restored – as well as de-facto raising XSS to the third place of the threat list. And, of course, it means that injection attacks are still among the most popular ones, and you need to take care of the secure code and input validation as ever.
A04:2021-Insecure Design
Now meet point 4, which ousted its predecessor, XML external entities (XXE). It’s totally new and called Insecure Design. Its purpose is to make cybersecurity specialists and developers focus on risks related to design flaws.
What does it mean. This change is extremely interesting because it goes much far than a regular technical vulnerability description — it’s a strategic thing. It’s about implementing security principles before your application is ready to go because insecure design flaws can hardly be fixed by the implementation of defense tools. Enhance, this point supposes conducting careful threat modeling and understanding most possible attacks vectors on the early stage to elaborate on required secure design patterns, principles, and architectures. Thus, if you did not think about security controls to fight back specific attacks in the early stage of creating your applications, it’s definitely a good time to start.
A05:2021-Security Misconfiguration
Point 5, Security Misconfiguration has moved up from position 6 in the previous list. This is a bad old kind of vulnerability popular in the wild. The only novelty is that now it includes XML External Entities (XXE) which was a separate point in the top 10 2017.
What does it mean. Actually, nothing new here – these kinds of vulnerabilities just has been transferred to the new list. What is worth mentioning, though, is that XXE vulnerability has been degrading significantly because of accelerating web developers’ switch from SOAP to REST. But it still can be met in many applications in the wild, so adding it to a wider category but keeping it in the list looks quite logical.
A06:2021-Vulnerable and Outdated Components
Now let’s jump to point 6, Vulnerable and Outdated Components. That’s just a twin of point 9 in top 10 2017 but under a different name. Before, it was called Using Components with Known Vulnerabilities.
What does it mean. Both the old and the new names clearly speak for themselves: If in your application you use a component with a known vulnerability, there is always a cybercriminal who will come to exploit it. Thus, the way is clear: Avoid using such vulnerable components and check all components you use for known vulnerabilities.
A07:2021-Identification and Authentication Failures
Point 7, Identification and Authentication Failures is a new name for Broken Authentication (not to be confused with Broken Access Control!) moved down from the second position in top 10 2017. And it’s not surprising, taking into attention that most web applications now utilize a ready-to-use framework that has secured identification and authentication standards by default. A strict requirement for password characters is a good example of this.
What does it mean. This change reflects the new trends in authentication processes. Maybe, you’ve noticed the revolution in this sphere is already upcoming. Microsoft is the first top-notch player that announced changing passwords for other means of authentication, and it’s just a beginning. We’ll inevitably see a fundamental change in authentication methods in the near future but until that you should take care of your passwords and cookies to meet the current security standards.
A08:2021-Software and Data Integrity Failures
Point 8, Software and Data Integrity Failures is another new category in the list. It focuses on software updates, critical data, and delivering a new version of software (CI/CD pipeline). This kind of vulnerability occurs when code and infrastructure do not protect against integrity violations. It can happen when an application relies upon tools from untrusted sources, be it plugins, libraries, or modules. Insecure CI/CD pipeline can cause unauthorized access, execution of malicious code, and the whole system compromise. Insecure Deserialization, that previously was honored to take a separate place in the top 10 2017, now is just a part of this category.
What does it mean. All of this may sound rather vague, but it becomes quite clear if you remember the Non-Petya ransomware attack back in 2016. The attackers substituted the legitimate update of accounting software for their malicious payload. As a result, all computers running the mentioned software downloaded the malicious update and got infected. Why could it happen? Because the update integrity was not verified properly. You may also remember plenty of other “supply chain” attacks. They are also related to this point.
And as the number of attacks of such kind is growing up with lightning speed, the appearance of this point in the top 2021 list looks pretty logical. In short, if you want to be secure, you need to be sure of the integrity of all the stuff your application use to work.
A09:2021-Security Logging and Monitoring Failures
Point 9, Security Logging and Monitoring Failures is also something reborn under the new name. In the top 10 2017, it was called Insufficient Logging & Monitoring and took the last place in the list. This point aims to help in the process of detecting, escalating, and responding to cyberattacks.
What does it mean. It might be the simplest category in the list to understand. If a cybersecurity incident will happen to you, how do you know what’s happened? What got infected and how? Where did the attack start? And how are you going to investigate the incident? The answer is nohow if you did not care to implement the logging and monitoring process in the proper way. So tune this up properly as soon as possible: Define what data are meaningful for this process and how to gather and store them reliably. That’s it.
A10:2021-Server-Side Request Forgery
And ultimately, we got to the last point in the list – point 10, Server-Side Request Forgery. From first sight, it may seem that a bad old Cross-Site Request Forgery (CSRF) has come back from the OWASP top 10 2013, but in reality, it’s not. The difference is in the first letter – “S” vs “C”. Cross-Site Request Forgery is a kind of client-side attack that was successfully mitigated in the last years, while the 2021 attack relates to servers – Server-side Request Forgery.
SSRF attack exploits a web application vulnerability when fetching a remote resource without validating the user-supplied URL is allowed. As a result, an attacker is able to send a forged request to internal company servers bypassing a firewall or VPN and conduct different kinds of malicious activity. According to OWASP, these kinds of attacks are increasing rapidly, especially because of a mass exodus of companies’ digital assets to the cloud – and that’s a solid reason for including it into the new top 10.
What does it mean. The cybersecurity landscape is changing quickly and types of prevalent attacks switch with these changes. Many client-side attacks become less popular because browser makers constantly install protection to prevent such attacks, while servers’ security is in the hand of their company owners. And as many of those owners don’t care much about such vulnerabilities, servers become easy prey for attackers. So you should be aware of this growing trend and prepare accordingly.
 What’s next?
What’s next?
One of the extremely important consequences of the new OWASP standard-setting is the necessity to review the security of web applications for companies around the world. Having your application audited under OWASP top 10 2017 is not enough anymore to consider it secure. It means that you need to conduct a new, based on OWASP top 10 2021 penetration test of your application.
We in DIESEC always keep our fingers on the pulse of rapid changes in the cybersecurity field. Our high-qualified penetration testers are ready to help you and test your application following the up-to-date OWASP top 10 2021 list. Contact us in any way convenient to you to find out the details.
Live secure with DIESEC!
