Was ist Datensicherheit?
Datensicherheit bezeichnet die Maßnahmen, die dazu beitragen, eine Organisation vor unbefugtem Zugriff auf ihre Daten zu schützen. Dazu gehören verschiedene Techniken wie Zugriffskontrolle, Verschlüsselung und Backup- und Restore-Prozesse. Die Einhaltung dieser Sicherheitsmaßnahmen ist unerlässlich, um sicherzustellen, dass Daten geschützt bleiben und nicht in die Hände von Unberechtigten gelangen.

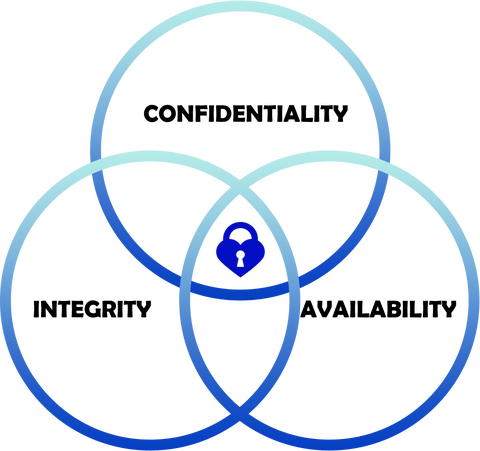
Warum ist Datensicherheit im Unternehmen wichtig?
Datensicherheit ist im Unternehmen von größter Bedeutung, da sie sicherstellt, dass sensible und vertrauliche Informationen nicht in die falschen Hände weitergegeben werden. Unzureichende Sicherheitsvorkehrungen können zu schweren Schäden für ein Unternehmen führen, da dieses dadurch anfällig für Cyberangriffe durch Fremde oder Insider wird. Außerdem kann es zu finanziellen Einbußen kommen, wenn Kundendaten gestohlen werden. Daher ist es unerlässlich, eine angemessene Sicherheitsarchitektur zu implementieren und regelmäßig zu überprüfen, um die Datensicherheit des Unternehmens zu gewährleisten.
Welche Arten von Datensicherheit gibt es?
Es gibt verschiedene Vorkehrungen, um die Datensicherheit einer Organisation zu schützen. Zu den häufigsten Sicherheitsmaßnahmen gehören physische Sicherheit, Netzwerksicherheit, Anwendungssicherheit und Datensicherung. Darüber hinaus gibt es auch Techniken wie Verschlüsselung, Benutzerauthentifizierung und Zugriffskontrolle, die eingesetzt werden können, um sensible Daten vor unberechtigtem Zugriff zu schützen.


Wie kann Datensicherheit im Unternehmen gewähleistet werden?
Um die Datensicherheit Ihres Unternehmens zu gewährleisten, empfiehlt es sich, einige vorbeugende Maßnahmen zu ergreifen. Zunächst sollten Sie eine vertrauenswürdige Sicherheitsarchitektur implementieren, um den Schutz personenbezogener Daten und anderer sensibler Informationen zu gewährleisten. Außerdem sollten Sie regelmäßig Software-Updates durchführen und effektive Techniken wie Verschlüsselung, Benutzerauthentifizierung und Zugriffskontrolle verwenden. Es ist auch ratsam, einen Notfallplan zu entwickeln sowie Mitarbeiterschulungen und Tests durchzuführen, um unautorisierte Zugriffe zu vermeiden.
Unsere zertifizierten, hocherfahrenen Experten bieten Ihnen professionelle Beratung zu Ihren speziellen Bedürfnissen. Gemeinsam werden wir ein leistungsstarkes System ausarbeiten und implementieren, um Ihre Daten am effektivsten zu schützen.
Sie interessieren sich für Datensicherheit?

Wenn Sie Fragen haben, können Sie sich gerne
an uns wenden. Wir freuen uns auf Ihre Nachricht.
